Chapter 1
The contents of this chapter are:
- Digital identity in the international market: analysis and problems
- What is a Federated Identity Management
- In-depth study of fiduciary models and authorization and authentication frameworks
- Problems and costs of federated and centralized models
- Case Studies: how SPID works, government identity provider service
Chapter 1
The contents of this chapter are:
- Digital identity in the international market: analysis and problems
- What is a Federated Identity Management
- In-depth study of fiduciary models and authorization and authentication frameworks
- Problems and costs of federated and centralized models
- Case Studies: how SPID works, government identity provider service
The theft of Digital Identities
Digital identity is your name, surname, address, telephone number, email, password, username, token, attributes, and secrets that you use to connect with others, that you use to find your personal data, or that you use to log in to an online and offline service.
Changing or acquiring a new or someone else’s identity, even for illegal purposes, is extremely easy. Over the course of 2018 in Italy alone, over 27,000 cases of credit fraud were carried out through identity theft, with an average amount of approximately € 5,000, with an economic loss of over € 152 million.
Discovery times tend to focus on two macro-categories mainly:
- 54% of cases are discovered within 6 months;
- only some of the rest emerge after 3, 4, and even 5 years.
The theft of Digital Identities
Digital identity is your name, surname, address, telephone number, email, password, username, token, attributes, and secrets that you use to connect with others, that you use to find your personal data, or that you use to log in to an online and offline service.
Changing or acquiring a new or someone else’s identity, even for illegal purposes, is extremely easy. Over the course of 2018 in Italy alone, over 27,000 cases of credit fraud were carried out through identity theft, with an average amount of approximately € 5,000, with an economic loss of over € 152 million.
Discovery times tend to focus on two macro-categories mainly:
- 54% of cases are discovered within 6 months;
- only some of the rest emerge after 3, 4, and even 5 years.
In the Black Markets, it is possible to find not only data relating to payment cards, but more and more frequently it is easy to come across sellers who also offer other services based on inevitable identity theft to facilitate the operations of their customers or to carry out fraud. more advanced.
How Online Identity Theft Can Happen?
Among the most used methods are:
- Social Engineering: exploiting user data to get to other personal information;
- Skimming: credit card cloning performed during the withdrawal operation;
- Bin raiding: retrieve tax information, bank statements, bills or any other documentation bearing personal information;
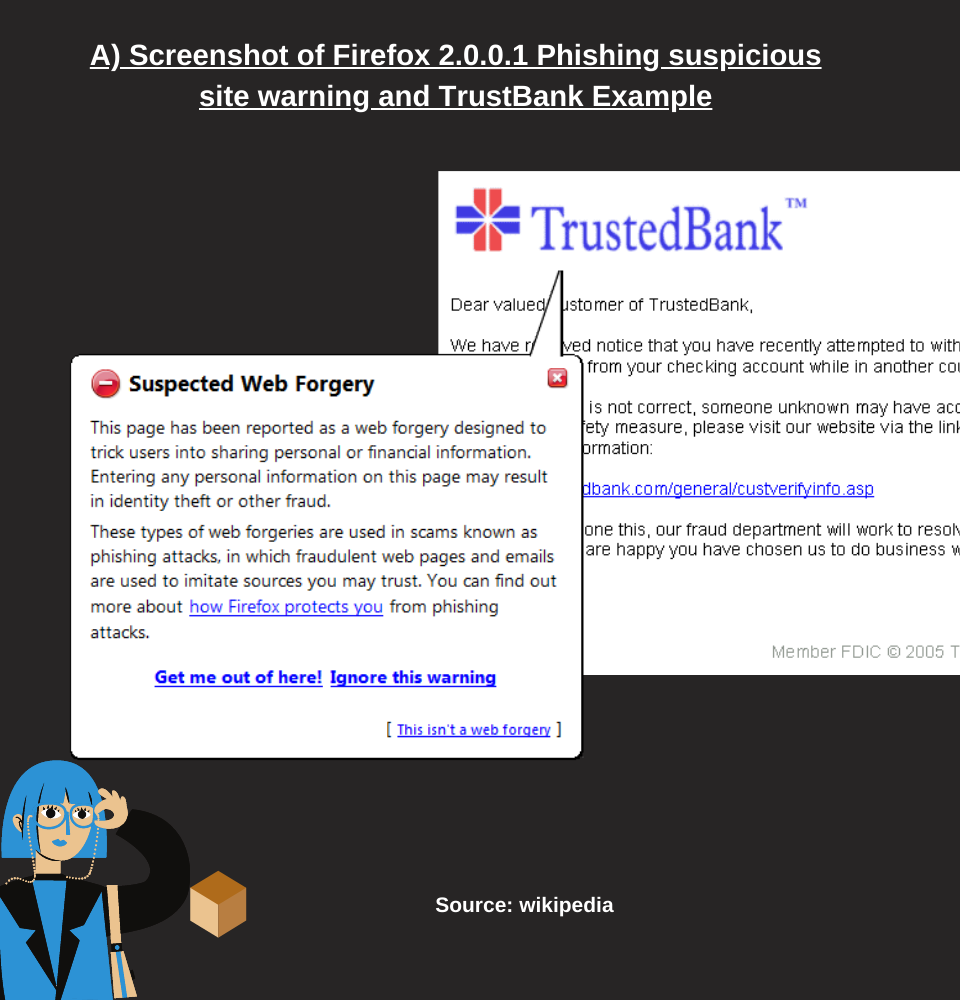
- Phishing: sending of personal e-mails and cleverly counterfeit advertising banners that can induce the user to communicate confidential information.
The 2-factor (2FA) or multi-factorial (MFA) authentication mechanisms are used in some services to guarantee the user greater control over their data. However, even with these tools, a hacker may be able to obtain other information relevant to our identity.

In the Black Markets, it is possible to find not only data relating to payment cards, but more and more frequently it is easy to come across sellers who also offer other services based on inevitable identity theft to facilitate the operations of their customers or to carry out fraud. more advanced.
How Online Identity Theft Can Happen?
Among the most used methods are:
- Social Engineering: exploiting user data to get to other personal information;
- Skimming: credit card cloning performed during the withdrawal operation;
- Bin raiding: retrieve tax information, bank statements, bills or any other documentation bearing personal information;
- Phishing: sending of personal e-mails and cleverly counterfeit advertising banners that can induce the user to communicate confidential information.
The 2-factor (2FA) or multi-factorial (MFA) authentication mechanisms are used in some services to guarantee the user greater control over their data. However, even with these tools, a hacker may be able to obtain other information relevant to our identity.
The markets of Digital Identity
Some considerations on the global digital identity market:
- among emerging economies, the digital identity market could reach an economic value equivalent to between 3% and 6% of GDP in 2030
- over a billion people worldwide do not have a verifiable identity
- the global market will grow from the US $ 23.3 billion in 2020 to the US $ 49.5 billion in 2026, recording a CARG of 16.2% from 2021 to 2026.
The market in Italy is still modest and very concentrated: from 2016 to the end of 2019, just over 7.5 million euros were spent by the public administrations for joining the SPID system, of which 5.7 million ( 76%) intended for only ten suppliers.
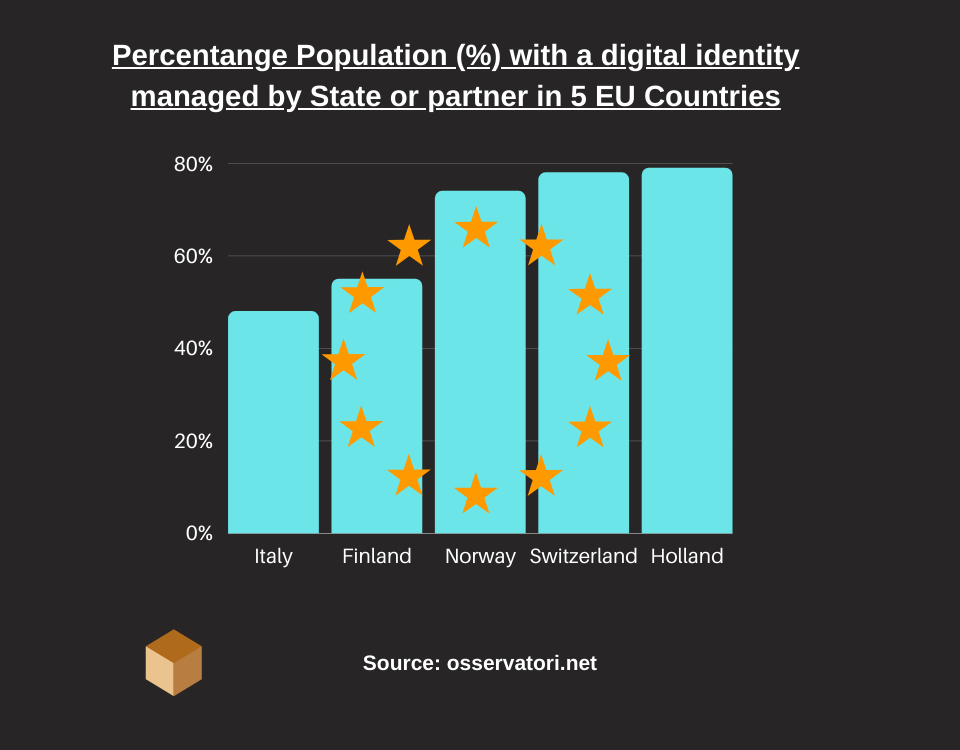
SPID covers 44% of the population, far from the levels of the more advanced European countries, such as the Netherlands (79%), Sweden (78%), Norway (74%) and Finland (55%).
There are 5,300 public administrations out of over 22,000 that allow citizens to use SPID to access at least one digital service.
The markets of Digital Identity
Some considerations on the global digital identity market:
- among emerging economies, the digital identity market could reach an economic value equivalent to between 3% and 6% of GDP in 2030
- over a billion people worldwide do not have a verifiable identity
- the global market will grow from the US $ 23.3 billion in 2020 to the US $ 49.5 billion in 2026, recording a CARG of 16.2% from 2021 to 2026.
The market in Italy is still modest and very concentrated: from 2016 to the end of 2019, just over 7.5 million euros were spent by the public administrations for joining the SPID system, of which 5.7 million ( 76%) intended for only ten suppliers.
SPID covers 44% of the population, far from the levels of the more advanced European countries, such as the Netherlands (79%), Sweden (78%), Norway (74%) and Finland (55%).
There are 5,300 public administrations out of over 22,000 that allow citizens to use SPID to access at least one digital service.

Tools like tokens, secrets, credentials and attributes will be explored later.

Who do we manage our data to and how is our identity managed on the web?
Identity management is achieved thanks to identity management systems, or a set of technologies that communicate identities in a common network. These are based on time-tested frameworks, IT protocols, and security models.
The models can be the “Scandinavian Model” if managed by private companies, while as “Continental Model” if managed by governmental entities.
The objectives of identity management are:
- Network identification
- Network authentication
- Network authorization

Tools like tokens, secrets, credentials and attributes will be explored later.

Who do we manage our data to and how is our identity managed on the web?
Identity management is achieved thanks to identity management systems, or a set of technologies that communicate identities in a common network. These are based on time-tested frameworks, IT protocols, and security models.
The models can be the “Scandinavian Model” if managed by private companies, while as “Continental Model” if managed by governmental entities.
The objectives of identity management are:
- Network identification
- Network authentication
- Network authorization
How are the actors of the identity model?
To describe the various management identity models, we first need to define the players:
- User: who owns the digital identity and wants to execute a transaction;
- Identity Provider (IdP): entity responsible for digital identity issuing and the implementation of the authentication mechanism;
- Service Provider (SP) or the Relying Party (RP): an entity or organization that provides a service to the user and that must verify the identity of the subject.
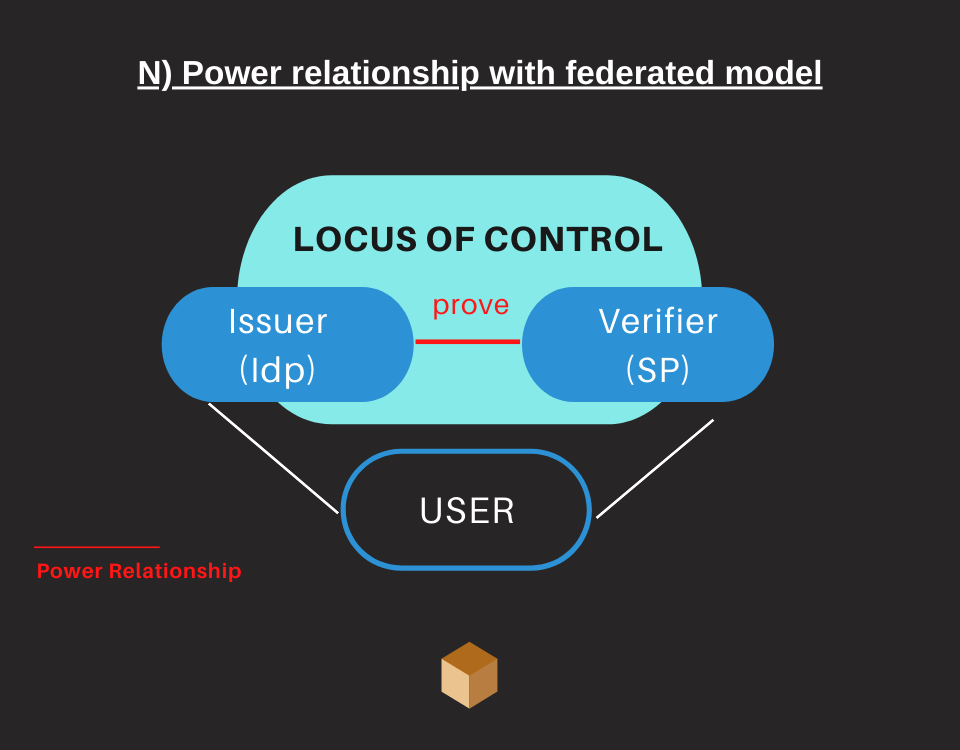
As of today, the actors communicate through two different systems:
- Centralized Model (Silos Model): the user has a direct relationship with the SP, who manages the personal data in his / her database
- Federated Model: the user does not have a direct relationship with the RP, while it is the IdP who manages the personal data in its database
How are the actors of the identity model?
To describe the various management identity models, we first need to define the players:
- User: who owns the digital identity and wants to execute a transaction;
- Identity Provider (IdP): entity responsible for digital identity issuing and the implementation of the authentication mechanism;
- Service Provider (SP) or the Relying Party (RP): an entity or organization that provides a service to the user and that must verify the identity of the subject.

As of today, the actors communicate through two different systems:
- Centralized Model (Silos Model): the user has a direct relationship with the SP, who manages the personal data in his / her database
- Federated Model: the user does not have a direct relationship with the RP, while it is the IdP who manages the personal data in its database
- First Chapter (%) 30%
Despite all the work carried out on federated identity since 2005, it is not yet able to provide us with the maximum degree of security in the use of our digital identity. This happens for a number of reasons:
- There is no one IDP that works with all sites and apps. Thus, users need more than one IDP;
- Many users and sites are reluctant to have a “middleman”;
- Large IDPs are susceptible to attacks from cybercriminals. Databases are frequently attacked by intruders via SQL Injection.
- The user has multiple identities that do not speak to each other
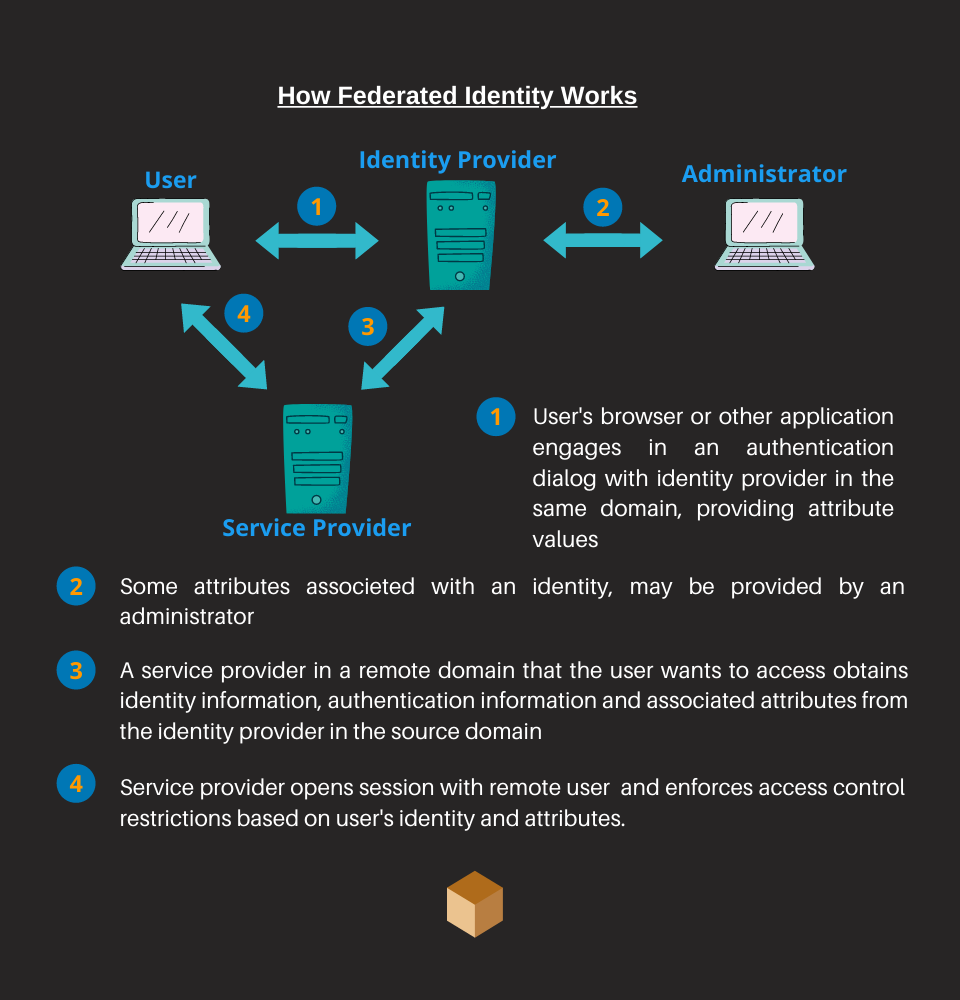
How the federated model works?
The federated model is the most used as it guarantees levels of interoperability and security. The role of the IdPs is predominant and they are referred to as federated IdPs.
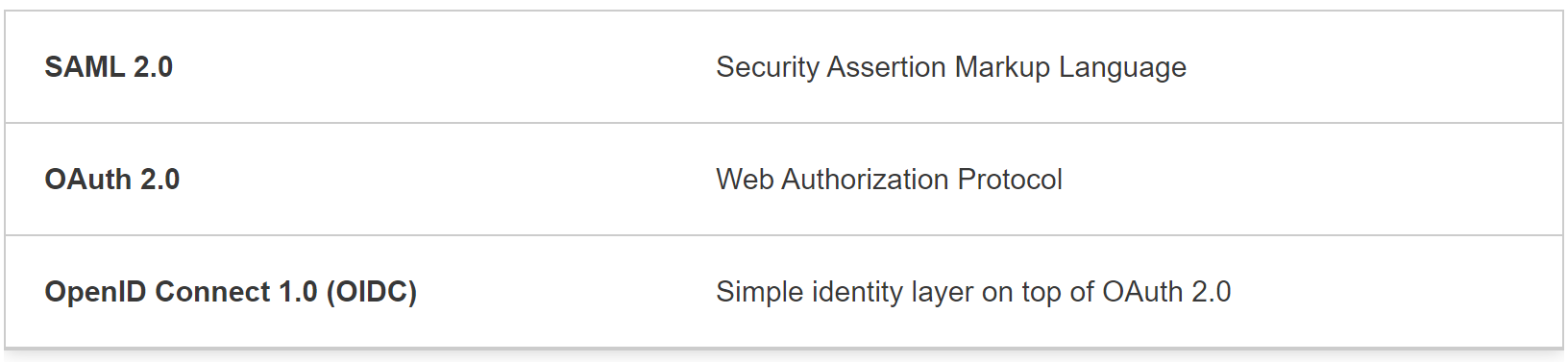
Three generations of federated identity frameworks/protocols have been developed since 2005:
- Security Assertion Markup Language (SAML),
- OAuth,
- OpenID Connect
Using OpenID Connect, logins via social networks such as Facebook, Google, Twitter, etc. they have become standard across websites.


- First Chapter (%) 30%
How the federated model works?
The federated model is the most used as it guarantees levels of interoperability and security. The role of the IdPs is predominant and they are referred to as federated IdPs.
Three generations of federated identity frameworks/protocols have been developed since 2005:
- Security Assertion Markup Language (SAML),
- OAuth,
- OpenID Connect
Using OpenID Connect, logins via social networks such as Facebook, Google, Twitter, etc. they have become standard across websites.

Despite all the work carried out on federated identity since 2005, it is not yet able to provide us with the maximum degree of security in the use of our digital identity. This happens for a number of reasons:
- There is no one IDP that works with all sites and apps. Thus, users need more than one IDP;
- Many users and sites are reluctant to have a “middleman”;
- Large IDPs are susceptible to attacks from cybercriminals. Databases are frequently attacked by intruders via SQL Injection.
- The user has multiple identities that do not speak to each other
Deepening of federated identity provider frameworks
The common objective of the 3 standard frameworks is to obtain a unique identification (Single Sign-On abbreviated as SSO) as a property of the control system and consequently:
- simplify the management of passwords
- simplify the management of access to the various services;
- Guarantee the safety and interoperability of systems and accesses
Thanks to these protocols relating to the authorization and access processes on the web, billions of users access online and offline services or information every day.
Deepening of federated identity provider frameworks
The common objective of the 3 standard frameworks is to obtain a unique identification (Single Sign-On abbreviated as SSO) as a property of the control system and consequently:
- simplify the management of passwords
- simplify the management of access to the various services;
- Guarantee the safety and interoperability of systems and accesses
Thanks to these protocols relating to the authorization and access processes on the web, billions of users access online and offline services or information every day.

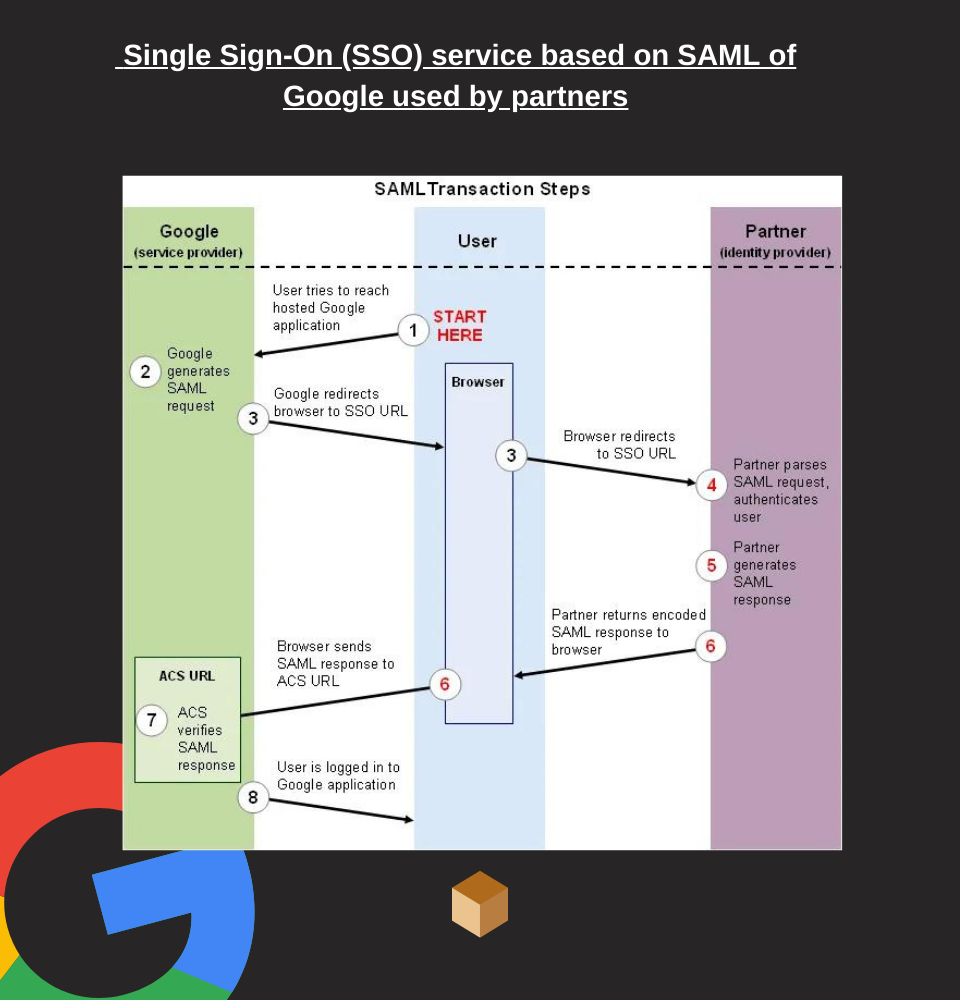
How does SAML 2.0 work?
SAML 2.0 (Security Assertion Markup Language) is a framework that authenticates and authorizes an IDP to pass an authentication token to an SP or RP.
SAML 2.0 refers to the XML variant language. The IDP transmits an XML document, the so-called SAML assertion to the SP when the user attempts to access these services. The SP requires authorization and authentication to the identifier from the IDP. When the IDP confirms, the user enters.
Two main security features of SAML
- Authentication
- Authorization

How does SAML 2.0 work?
SAML 2.0 (Security Assertion Markup Language) is a framework that authenticates and authorizes an IDP to pass an authentication token to an SP or RP.
SAML 2.0 refers to the XML variant language. The IDP transmits an XML document, the so-called SAML assertion to the SP when the user attempts to access these services. The SP requires authorization and authentication to the identifier from the IDP. When the IDP confirms, the user enters.
Two main security features of SAML
- Authentication
- Authorization
How does oAuth2 and OpenID Connect work?
oAuth 2 is a standard authorization framework for web applications.
OAuth2 defines 4 roles:
- Resource Owner: generally themselves (user).
- Resource Server: server that collects user data
- Client: App that requires access to the Resource Server
- Authorization Server: Server that issues the access token to the client. The token will be used by the client to access the resource server. Often the Resource server coincides with the Authorization server.
OpenID Connect (OIDC) is an infrastructure built on top of OAuth 2.0 that adds login and profile information of the person who, through login, email, and password associated and cryptographically correct, receives the token to access a service or enter the portal.
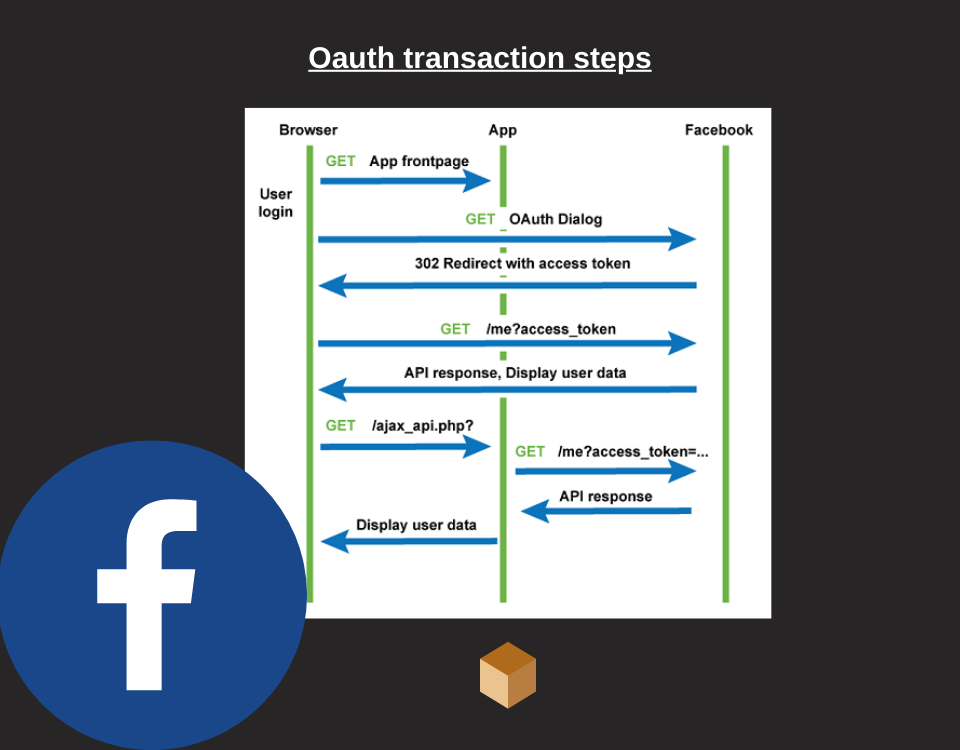
How is access guaranteed?
The website we want to access via Facebook receives an access token from the oAuth 2 Server. When the website calls the API for the information, it delivers the received token and thus is granted access. oAuth 2 does not specify how this token should be verified.
The choice that is regularly implemented is to issue a token with limited and self-referential time validity, i.e. signed with asymmetric cryptography: a JWT.
In this way, the website has a time window to access the requested information and cannot change its access rights because it does not have the private key to change the token.
How does oAuth2 and OpenID Connect work?
oAuth 2 is a standard authorization framework for web applications.
OAuth2 defines 4 roles:
- Resource Owner: generally themselves (user).
- Resource Server: server that collects user data
- Client: App that requires access to the Resource Server
- Authorization Server: Server that issues the access token to the client. The token will be used by the client to access the resource server. Often the Resource server coincides with the Authorization server.
OpenID Connect (OIDC) is an infrastructure built on top of OAuth 2.0 that adds login and profile information of the person who, through login, email, and password associated and cryptographically correct, receives the token to access a service or enter the portal.

How is access guaranteed?
The website we want to access via Facebook receives an access token from the oAuth 2 Server. When the website calls the API for the information, it delivers the received token and thus is granted access. oAuth 2 does not specify how this token should be verified.
The choice that is regularly implemented is to issue a token with limited and self-referential time validity, i.e. signed with asymmetric cryptography: a JWT.
In this way, the website has a time window to access the requested information and cannot change its access rights because it does not have the private key to change the token.
- OpenID Connect further expands this to allow obtaining the identity without this additional step involving calling from the application to the identity provider.
- OAuth 2.0 is a framework that controls the authorization for access to any protected resource, while OpenID Connect and SAML 2.0 are both standards referring only to the federated model.
Differences and similarities of frameworks:
The decision to use a framework rather than another is not always immediate. Many struggles to grasp the differences between OAuth 2.0, OpenID Connect, and Security Assertion Markup Language (SAML).
- SAML 2.0 creates a trust relationship on a digital signature. In fact, the SAML tokens issued by the identity provider are XML-signed, the application validates the signature itself and the certificate it presents.
- SAML 2.0. is independent of OAuth.
- OAuth2 creates the trust relationship on a direct HTTP call from the application to the identity.

Differences and similarities of frameworks:
The decision to use a framework rather than another is not always immediate. Many struggles to grasp the differences between OAuth 2.0, OpenID Connect, and Security Assertion Markup Language (SAML).
- SAML 2.0 creates a trust relationship on a digital signature. In fact, the SAML tokens issued by the identity provider are XML-signed, the application validates the signature itself and the certificate it presents.
- SAML 2.0. is independent of OAuth.
- OAuth2 creates the trust relationship on a direct HTTP call from the application to the identity.
- OpenID Connect further expands this to allow obtaining the identity without this additional step involving calling from the application to the identity provider.
- OAuth 2.0 is a framework that controls the authorization for access to any protected resource, while OpenID Connect and SAML 2.0 are both standards referring only to the federated model.
Problems and costs of federated models for the IdPs
The main security and resource problems that an identity provider must address mainly include:
- Data leak: unauthorized transmission of data from within an organization to an external recipient where the main cause is human error.
- Data loss: error condition in information systems due to failures or negligence in archiving, transmission or processing.
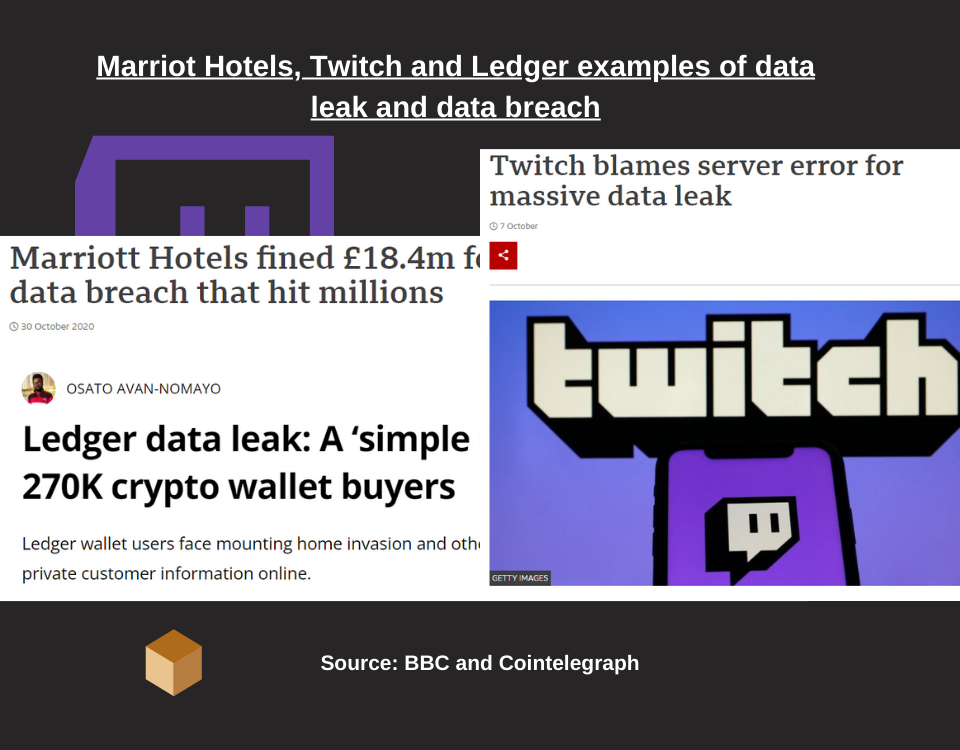
- Data breach: security breach by a hacker that involves the destruction, loss, modification, unauthorized disclosure or access to personal data transmitted, stored or otherwise processed.
- Scalability: infrastructure ready to scale in moments of maximum client demand (user stress testing)
Data leak, data loss and data breach are evidence of a problem referred to as Single-Point-Of-Failure (SPOF): one weakness, lots of data.
Problems and costs of federated models for the IdPs
The main security and resource problems that an identity provider must address mainly include:
- Data leak: unauthorized transmission of data from within an organization to an external recipient where the main cause is human error.
- Data loss: error condition in information systems due to failures or negligence in archiving, transmission or processing.
- Data breach: security breach by a hacker that involves the destruction, loss, modification, unauthorized disclosure or access to personal data transmitted, stored or otherwise processed.
- Scalability: infrastructure ready to scale in moments of maximum client demand (user stress testing)
Data leak, data loss and data breach are evidence of a problem referred to as Single-Point-Of-Failure (SPOF): one weakness, lots of data.
What are the costs of businesses for low security?
Ponemon‘s recent “Cost of a Data Breach 2020” report has returned some interesting data on the phenomenon and how it has developed this year:
- the average cost for Data Breach goes from 2.92 million dollars to 3.86 million;
- an average of $ 146 for a single data record, which rises to 150 if it contains personal data;
- breaches from 1 million to 10 million records cost an average of $ 50 million, more than 25 times the average cost of $ 3.86 million for breaches of less than 100,000 records;
- in violations involving more than 50 million records, the average cost was $ 392 million, more than 100 times the average.
- First Chapter (%) 91%
The sectors most affected by cyber-attacks were financial services (171 euros for stolen information), the energy sector (165 euros), and the pharmaceutical sector (164 euros).
What are the costs of businesses for low security?
Ponemon‘s recent “Cost of a Data Breach 2020” report has returned some interesting data on the phenomenon and how it has developed this year:
- the average cost for Data Breach goes from 2.92 million dollars to 3.86 million;
- an average of $ 146 for a single data record, which rises to 150 if it contains personal data;
- breaches from 1 million to 10 million records cost an average of $ 50 million, more than 25 times the average cost of $ 3.86 million for breaches of less than 100,000 records;
- in violations involving more than 50 million records, the average cost was $ 392 million, more than 100 times the average.

- First Chapter (%) 91%
The sectors most affected by cyber-attacks were financial services (171 euros for stolen information), the energy sector (165 euros), and the pharmaceutical sector (164 euros).

Verification of a user’s identity takes place through the exchange of data, called assertions. Each assertion, therefore, makes it possible to ascertain that authentication took place correctly at a given moment in time and with a correct authentication method. The exchange of such information takes place between an IdP and an SP.
Through the IdP software, the user receives an OTP (One-Time-Password) generated and visible to both the user and the IdP. This mechanism reinforces the security of the identification process, it is defined as two-factor authentication (2FA).
Federated digital identity in Italy: how SPID works
The Public Digital Identity System (SPID) is a digital identity consisting of a username, password and token. These strictly personal data enable the identification of the citizen and the use of online services of the public administration and private adherents.
The security protocol on which the SPID digital identity is based is SAML 2.0. and it is a federated model.
SPID is a federated management system and includes several subjects:
- Italian citizen (user)
- the digital identity manager (IdP). This is a subject, which must be accredited by the Agency for Digital Italy the manager of qualified attributes who can certify qualified attributes, such as the possession of a qualification, membership of a professional order;
- the public or private Service Provider (SP).

Verification of a user’s identity takes place through the exchange of data, called assertions. Each assertion, therefore, makes it possible to ascertain that authentication took place correctly at a given moment in time and with a correct authentication method. The exchange of such information takes place between an IdP and an SP.
Through the IdP software, the user receives an OTP (One-Time-Password) generated and visible to both the user and the IdP. This mechanism reinforces the security of the identification process, it is defined as two-factor authentication (2FA).
Federated digital identity in Italy: how SPID works
The Public Digital Identity System (SPID) is a digital identity consisting of a username, password and token. These strictly personal data enable the identification of the citizen and the use of online services of the public administration and private adherents.
The security protocol on which the SPID digital identity is based is SAML 2.0. and it is a federated model.
SPID is a federated management system and includes several subjects:
- Italian citizen (user)
- the digital identity manager (IdP). This is a subject, which must be accredited by the Agency for Digital Italy the manager of qualified attributes who can certify qualified attributes, such as the possession of a qualification, membership of a professional order;
- the public or private Service Provider (SP).
Verification of a user’s identity takes place through the exchange of data, called assertions. Each assertion, therefore, makes it possible to ascertain that authentication took place correctly at a given moment in time and with a correct authentication method. The exchange of such information takes place between an IdP and an SP.
Through the IdP software, the user receives an OTP (One-Time-Password) generated and visible to both the user and the IdP. This mechanism reinforces the security of the identification process, it is defined as two-factor authentication (2FA).